25 Apr 2026
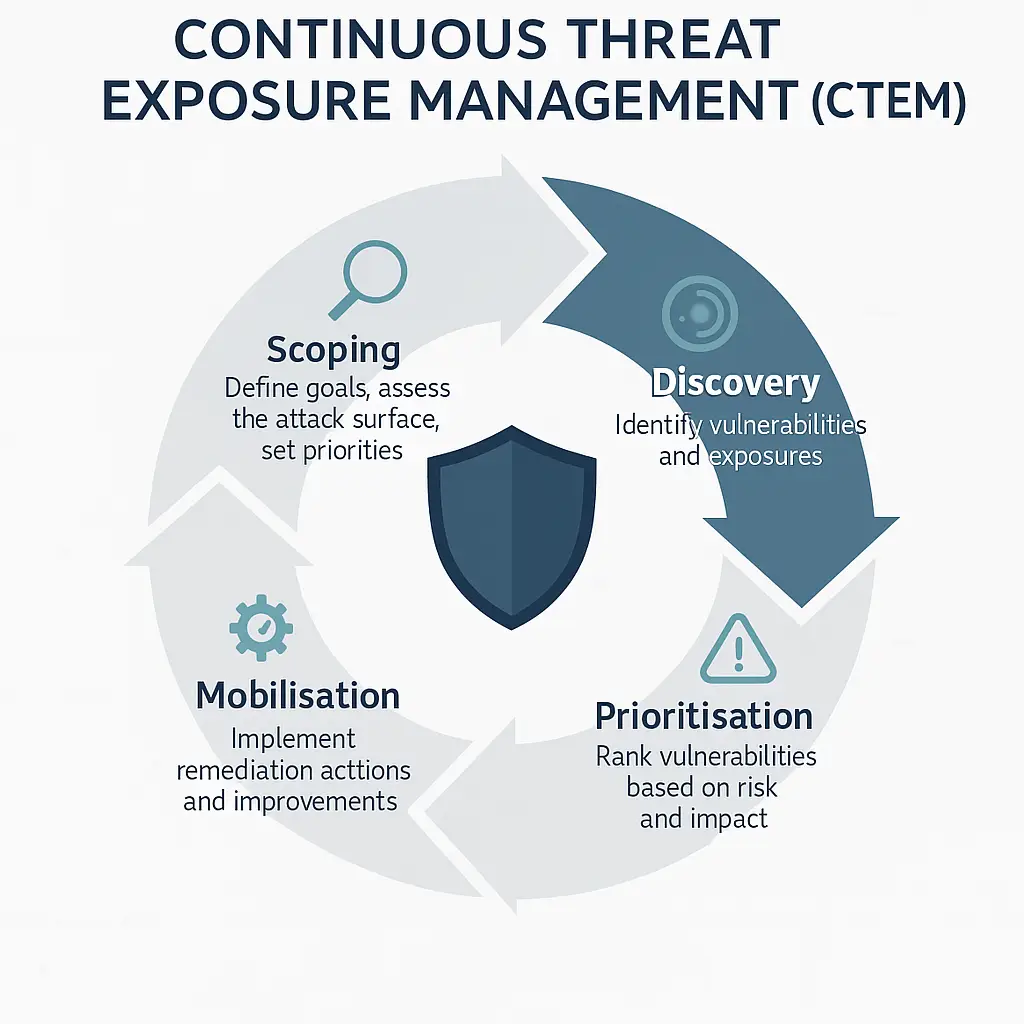
In today’s rapidly evolving cyber threat landscape, organisations in high-risk sectors – from financial services and banking to legal, logistics, and research – are increasingly asking: “What is SOC?”. A Security Operations Centre (SOC) is a dedicated hub of people, processes, and technology focused on 24/7 cybersecurity monitoring and incident response. In the UK, senior decision-makers such as CISOs, IT managers, Security Engineers, and CTOs recognise that having a robust SOC is essential for protecting sensitive data and maintaining trust. This article provides a detailed, educational overview of what a SOC is and how it operates, tailored for a professional audience. We will explore the SOC’s definition and purpose, its history and evolution, core components and functions, the key roles on a SOC team, and the technologies they use. We’ll also discuss the business benefits of having a SOC, compare building an in-house SOC versus using an outsourced SOC-as-a-Service, and examine how UK Cyber Defence’s “Detect, Defend, Disrupt” approach sets it apart from competitors like Quorum Cyber and Arctic Wolf. Finally, we’ll look at future trends in SOC development and cyber defence, and conclude with guidance on leveraging SOC-as-a-Service to enhance your organisation’s security posture.
Read article