11 Aug 2026
The Growing Threat of DDoS Attacks And How to Defend Against Them
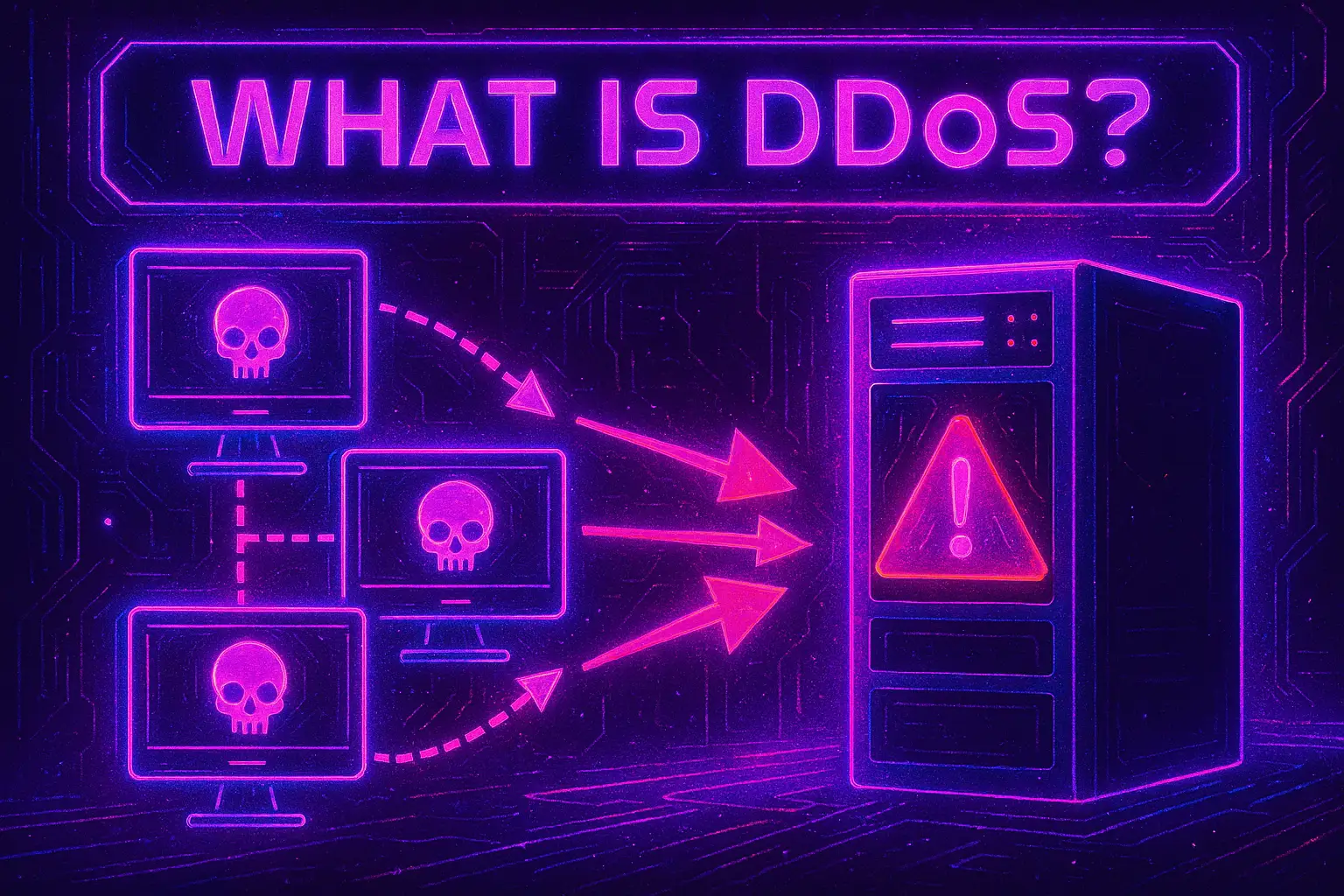
ADistributed Denial of Service (DDoS) attackis a malicious attempt to disrupt the normal traffic of a targeted server, service, or network by overwhelming it with a flood of traffic from multiple sources. Unlike a basic Denial of Service (DoS) attack, which comes from a single source, DDoS attacks leveragebotnets— networks of compromised devices — to amplify their impact and make them harder to stop.
Read article